- Barajar
ActivarDesactivar
- Alphabetizar
ActivarDesactivar
- Frente Primero
ActivarDesactivar
- Ambos lados
ActivarDesactivar
- Leer
ActivarDesactivar
Leyendo...
Cómo estudiar sus tarjetas
Teclas de Derecha/Izquierda: Navegar entre tarjetas.tecla derechatecla izquierda
Teclas Arriba/Abajo: Colvea la carta entre frente y dorso.tecla abajotecla arriba
Tecla H: Muestra pista (3er lado).tecla h
Tecla N: Lea el texto en voz.tecla n
![]()
Boton play
![]()
Boton play
![]()
15 Cartas en este set
- Frente
- Atrás
|
Amazon Simple Notification (Amazon SNS) and Amazon Simple Queue (Amazon SQS) services for decoupling.
|
|
|
Classic, application, and network load balancers
|

|
|
Route 53 for DNS and service discovery
|

|
|
Identity and Access Management (IAM) for authentication and authorization.
|

|
|
Secrets Manager for managing encrypted passwords, credentials, tokens, and other secrets.
|

|
|
API Gateway to expose the services to the outside world.
|

|
|
AWS developer tools, such as CodePipeline, for CI/CD.
|

|
|
Amazon CloudWatch for monitoring, logging, and alerting.
|

|
|
EKS Integration example
|
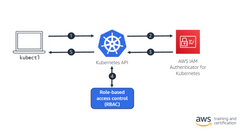
The authenticator is a tool to use AWS IAM credentials to authenticate to a Kubernetes cluster. By using AWS IAM Authenticator for Kubernetes, you avoid having to manage a separate credential for Kubernetes access.
|
|
Single Sign On (SSO) in EKS
|
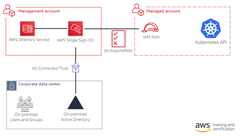
You should consider a few prerequisites:
1. You must enable the organizations. The Kubernetes cluster must reside in a non-management account managed by organizations with all features enabled. 2. Your Active Directory (AD) must be an AWS Managed AD, must use AD Connector, or must have a trust established for an AWS managed AD. 3. You must enable SSO in the management account and attach it to the AD. |
|
ConfigMaps
|
ConfigMaps allow you to store configurations for Kubernetes applications separately and refer to them when needed. Many applications require configuration through some combination of config files, command-line arguments, and environment variables. Data is stored in ConfigMaps as key-value pairs, but you can inject data from ConfigMaps into your application in various ways. You shouldn't store sensitive information, such as database passwords, in ConfigMaps. To store sensitive information, you should use secrets, which we will discuss later.
In this example, we create a new ConfigMap named "my-config" from the file named "myparams". When you create a ConfigMap using the --from-file option, by default, the filename becomes a key stored in the data section of the ConfigMap. In this example, the key is “myparams” and the value is the whole contents of the specified file. If you want to define multiple key-value pairs from a single file, you should use the --from-env-file option instead. |
|
Secrets
|
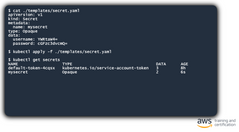
Sensitive information should be stored as secrets. The Kubernetes secret object allows you store and manage sensitive information, such as passwords, tokens, and ssh keys. In this example, the secrets have been encoded and written to a configuration file. Next, we create a "secret" object and confirm that the secret is present in Kubernetes. The values of the secret are displayed as "Opaque".
|
|
Configruging a Pod to access Secrets
|
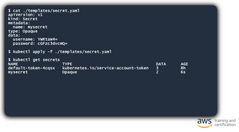
Here is an example of consuming the secret as a pod environment variable. As with ConfigMaps, it would be an option to consume the secret as a pod volume instead, if desired.
|
|
Integrating Secrets Manager with EKS
|
In EKS, you can also store and retrieve secrets from the parameter store, which is integrated with AWS Secrets Manager. AWS Secrets Manager allows you to easily rotate, manage, and retrieve database credentials, API keys, and other secrets throughout their lifecycle.
|
|
DaemonSets in EKS
|
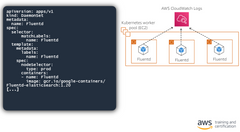
A DaemonSet is a type of controller that makes sure that all nodes have a copy of the requested pod. This is useful to provide common supporting functionality (such as security, logging, monitoring, or backups) for the pods running your application code. Deleting a DeamonSet will delete any pods it created across all the nodes.
|